what can a browser hijacker do If it Enter in your System
How Browser Hijackers Infect Computers an What Can It Do
Browser hijacking is termed as a serious security violation application. If any hijacking application has overridden over your browser, and it starts affecting most of the personal or sensitive information stored then it is a severe threat. Browser hijackers in most of the cases because of its nature, make it difficult to browser normally and can open up your computer to a host of additional infections. Here a Gudie to Remove Browser Hijacker in your Phone.

Unknown Homepage and URL Redirecting
One of the most common signs of browser hijacking is to find out that your homepage has been reset without your permission. If your frequently used browser shows unfamiliar website after launch, and in particular that is pornographic or advertising fake security software, this is most definitely the hijacker at play. A post is entering any URL in your search bar; you find yourself getting redirected to different website than the one you intended, indicates a hijacker infection in your computer. Once you discover that you are getting redirected, you will be able to reset your homepage immediately, but it will probably return to the hijacked state once you relaunch your browser. To get your settings back to normal, it is advisable to remove the hijacker.
Unstoppable Pop Ups
People think pop ups as a bit irrupting and hindrance in your browsing activity, but popups are in reality form of malware on your browser hijackers. Hijacked browsers frequently show an unstoppable outburst of popup ads, and hijackers can even disable your browser's popup blocker. The main aim of these never-ending popups is to get you to click on one of the links by mistake and give way to the virus to creep into your computer, thus installing rogue programs. These links also try to redirects you towards nasty websites.

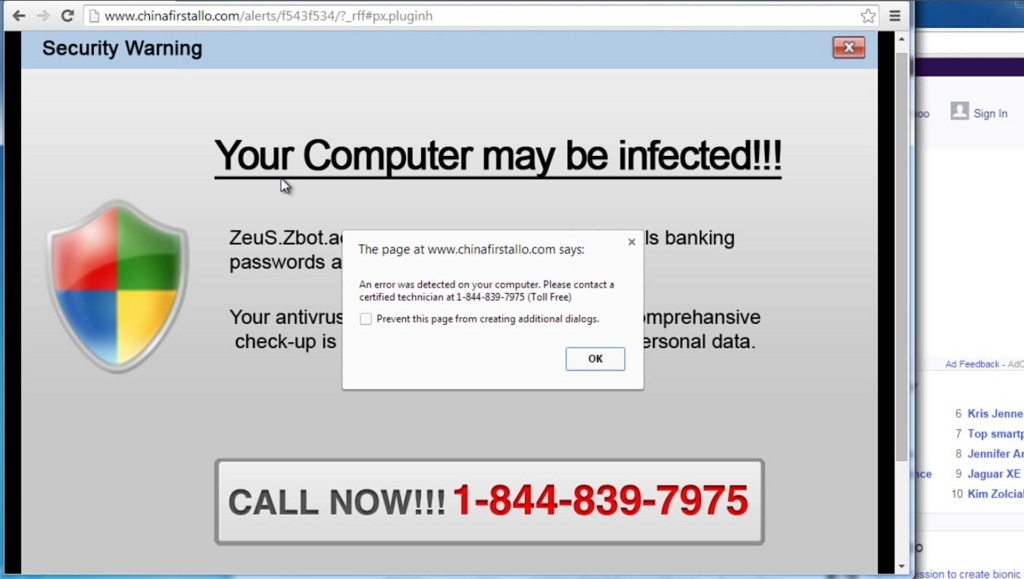
Fake Security Alerts
The fake security alert is another type of popup hijackers. The frequently used browser or desktop shows a flood of popup message which states that your computer is being hacked or that your security has been corrupted, stop and take some time to read the message in full before clicking on any links. If you feel these are a fake message because it is blocking your security program that you don't remember installing, then it is a good possibility that this is the work of a hijacker. As these messages are designed to look like legitimate system alerts, look carefully for any discrepancies, such as colors that vary from your desktop color scheme or obvious spelling errors.
Suggestions and Solution
If you doubt that your browser has been hijacked, the first step should be to shut you’re your computer immediately.
To protect and secure your computer we would like to suggest to install our free antivirus tool Malware Crusher and do a full system scan with your antivirus software, which should be able to remove the hijacker software.
Post the scan is complete and the hijacker is completely removed, it is advisable to perform a reinstall of your browser software so to erase any changes that the hijacker has made.
It is assumed that most browser hijackers are piggyback for third-party browser add-ons, it is suggested that if you need to download add-ons choose a reliable source approved by your browser's developer. It is also a good habit to change all of your passwords after a hijacker infection.
While installing any new freeware software or new game, always go through the license agreement section and read all the terms and conditions.
If reading terms and condition is time-consuming, so be careful while installing freeware go for the option “custom and automatic installation,” it is suggested that you go with this option, this will ensure the closure of the other programs that might get installed along with it. So to secure all these issues use the best antivirus tool Malware Crusher.
Another task on the part of the user is the negligence, if you find your computer screen bombard with any additional add-ons or toolbars pre -checked, then make sure to uncheck them to avoid the installation of browser hijacker or the adware.
How to Get Infected With Malware
Back in the beginning of PCs, each client required a goodly dab of specialized skill. Something not working? Open the case and reseat all the extension cards, maybe, or clean the terminals with a pencil eraser. Request help at the PC Users' Group meeting. Have a go at tweaking a few settings in the CONFIG.SYS record. Fun stuff! However, that period is a distant memory. Present day processing gadgets simply work, more often than not, which can be so exhausting. Here's an idea to flavor up your life—for what reason not get your computer infected with malware?
Consider the possibility that you turned on your computer and it flashed a notice that the FBI is researching you. Or then again opened your browser just to go up against a snow squall of fun and vivid advertisements? Who knows, perhaps your computer could be among the zombie armed force enrolled by a bot herder to bring down a noteworthy site! Wouldn't that be cool?
In truth, on the off chance that you need to open yourself to the full malware encounter, you will need to complete a little work. Current working frameworks and computers are simply too darn babysitter state defensive. Here are a few hints to slide you into this energizing world.
Pick the Right Device
Love your Mac? Your iPad Pro? Indeed, for the present, you'll need to set them aside. There's most likely that malware for macOS exists, however you could get old and dark holding up for an attack to hit. Concerning iOS, forget about it! Everything that raises macOS hell when you're endeavoring to get malware goes twofold for iOS.
What you require is a decent old PC, running Microsoft Windows. The more seasoned the Windows form the better; more up to date editions make them bother worked in security highlights. On the off chance that you can discover a case running the antiquated Windows 95, that is brilliant! Microsoft finished help for this valuable antique working framework in 2001, and programmers have had a very long time to misuse it.
On the off chance that you can't concoct a Windows gadget, go for Android. That is the thing that the malware scholars do! Bunches of Android gadgets stall out at an old Android rendition in light of the fact that the merchant doesn't bolster refreshes, including security refreshes. Candy, anybody? Android fracture implies that there are a considerable measure of defenseless telephones out there.
Read Aslo How to remove shortcut virus
Malware Protection
In case you're striving for the malware infection encounter, clearly you don't need malware insurance installed. That would nullify the general purpose! Be that as it may, hang tight, don't simply delete your antivirus; it's not as simple as that.

It couldn't be any more obvious, Microsoft super needs you to have some sort of antivirus assurance. In the event that Windows 10 recognizes that you don't have some other antivirus running, it naturally turns on Microsoft Windows Defender Security Center. Previously, that wouldn't have been an issue, since Windows Defender was so faltering. Yet, sadly, the most recent variant is indicating better test outcomes.
You may figure you can kill Windows Defender by delving into security settings and turning Real-time assurance off. In any case, Defender continues running booked outputs, with the goal that's not a genuine arrangement. Truly, in case you're a PC wizard you can edit the Registry to put a stake through Windows Defender's heart. It is safe to say that you are a wizard? I didn't think so.
Your most solid option is to check our surveys of antivirus software and pick one with a poor score. You can likewise have a go at keeping the antivirus program dynamic, yet handicapping booked sweeps and continuous assurance. Even better, utilize a more seasoned adaptation of Windows, one without all the security cushioning.
Tell the Browser to Shut Up
Present day browsers think they know everything. Download this, yet don't download that. This site is OK, however you can't go to that one. Divert from the oppression of the browser! You're the one in control, all things considered.
Normally, the way you escape persecution varies between browsers. In Chrome, click Settings from the menu, click Advanced, and simply kill everything under Privacy and Security. In case you're inclined toward Edge, pick settings from the menu, click View propelled settings, look to the base, and kill Windows Defender SmartScreen.
Firefox clients should click Options, select the Privacy and Security tab, and un-check the case titled Block perilous and misleading substance. On old fashioned Internet Explorer, press Alt+T to raise the Tools menu, select Windows Defender SmartScreen Filter, and kill that component.
Read Also Basic Tips on Computer Security For Beginners
we infect computers with malware intentionally, to test security items, and we have our own particular techniques for gathering malware tests. In case you're eager to kick the malware party off, there are a lot of assets accessible to general society, among them the Contagio Malware Dump site and the KernelMode.info malware talk gathering.That is it! You're allowed to surf all the web, not only the spots your downer browser grants. Look at shady connections, offensive sites, locales offering free utilities, wherever you can envision.
Click All the Links!
Alright, you've removed the deterrents to procuring a malware infection. Presently what? Where's the malware?
To begin with stop—your email account. Avoid those recognizable messages from your supervisor, and your Aunt Esther. Search for weirdo messages from new people. In the event that you don't discover them, check the garbage mail organizer. When you locate an offer to meet a Russian lady, or get millions from your missing Nigerian cousin, tap the connection to perceive what they need to indicate you.
On the off chance that the site page shows you have to install another video codec or driver or whatever, proceed! It may be an exhausting refresh, yet it could be some cool malware. On the off chance that you don't see anything intriguing, don't surrender. Some malware works off camera. Yet, in the event that you're fortunate you may see an engaging screen like the one beneath. Try not to stress; the FBI isn't generally after you. This malware is simply feigning.
Get Free Storage With Free Malware
You don't pay for USB thumb drives, isn't that right? That is to say, individuals are giving them away everywhere. Go to a course, you get the content on a thumb drive. Your children may expedite homework from school a thumb drive. On the off chance that you can wangle your way into the Press Room at Black Hat or another security meeting, you'll discover an abundance of public statements on thumb drives. The exhausting security wonks don't take them, with the goal that leaves all the more for you.
You've heard the articulation, "See a penny, lift it up, all the day you'll have good fortunes." Well, doubtlessly it's far superior fortunes to discover a thumb drive on the walkway, or in the parking area!
Most USB malware is sufficiently affable to dispatch consequently when you connect to the drive. In the case of nothing dispatches, investigate what's on the drive, see what sort of intriguing programs are sitting tight for you to enact them.
In case you're utilizing a more established computer, you could be in for some free firecrackers. Initially showed at Black Hat, now promoted as an apparatus for testing, the USB Killer utilizes your computer's own particular USB capacity to energize its capacitors, at that point destroy the PC with 200 volts. On the off chance that the equipment isn't appropriately supported, the outcomes can be energizing.
Try not to be disillusioned if the thumb drive doesn't appear to contain anything intriguing. It could be subtly assuming control over your PC with no unmistakable confirmation. What's more, if nothing else, you got yourself a free thumb drive!
Protect your computer from online hackers
In today’s digital world we all use the internet in some aspects of our lives. We go online for all kinds of information, doing online shop, and banking, keep the household metrics, play games, and stay in touch with family and friends through social networking. So, our devices hold a lot of wealth of personal information about us. This may include banking and other financial records, and medical information—information that we want to protect. Get Best Antivirus for windows 10 for protect your system.
If your devices is not secure and protected, identity thieves and other cheats are able to get access and steal your personal information.
The following tips will help the victim to lower your risk while you're online.
Keep your device secure
The most important thing as a user is to make sure to keep device secure. Be aware to any latest news and downloads recommended updates from your device's and its manufacturer or operating system provider, especially for important software such as your internet browser. Antivirus software, antispyware software, and firewalls are also important tools to prevent attacks on your device.
Keep up-to-date
The need of the hour is to keep your system update, browser, and important apps regularly, taking advantage of automatic updating when it's available. For mobile devices, be sure to install Android or iPhone updates that are distributed automatically.
Antivirus software protects your device from viruses that can destroy your data, slow down or crash your device, or allow spammers to send email through your account. Antivirus helps you scans your files and any incoming email infected with viruses, and evaluates and deletes anything malicious. Set an automatic your antivirus software to check for viruses every day. As a precaution It is a good habit to give your system a thorough scan at least twice a month.
The nastiest virus is a spyware, these software gets installed on the victim’s computer without their knowledge or consent and has the ability to monitor your online activities and collect personal information while you're online. Few example of spyware are like the keyloggers, record everything you key which includes your passwords and financial information. Some of the spyware’s comes with a predetermined protection in few antivirus software programs.
To sidestep spyware entering your computer download software only from sites you know and trust. Make sure apps you install on a mobile device come from the Apple App Store for iPhones or Google Play for Android devices.
Firewalls
This software is very useful as it blocks hackers from entering and using your computer. Firewalls prevent your computer from reacting to any harmful random calls. A firewall works as a wall wherein it blocks communications to and from sources from whom you don't permit. In case of high-speed internet this is especially important. Few OS have in build firewalls, make sure to turn your firewall on. To be effective, your firewall must be set up properly and updated regularly. Check your online "Help" feature for specific instructions.
Read Also Best Browser hijacker removal tool for windows 7
Choose strong passwords
To safeguard and protect your devices and accounts from hackers choose a passwords that is hard to guess. Use strong passwords with at least eight characters, a combination of letters, numbers and special characters. Don't use a word that can easily be found in a dictionary or any reference to personal information, such as a birthday. Pick an unusual and unique passwords for each online account you use: financial institution, social media, or email. We all use some many apps and software so sometimes it gets difficult to remember all the password consider using password manager software, which can help you create strong individual passwords and keep them secure.
Use stronger authentication
Few social networking and media, email, and financial accounts permit the use of stronger authentication methods. These methods can include using a fingerprint, one-time codes sent to a mobile device, or other features that ensure a user is supposed to have access to the account.
Suggestions and Solution
If you suspicious that your browser has been hijacked, shut it down instantaneously.
Install our free malware tool and do a full system scan with your antivirus software, which should be able to remove the hijacker software.
After scan is done and the hijacker is completely removed, perform a reinstall of your browser software so to erase any changes that the hijacker has made.
If reading terms and condition is time consuming , then install the freeware opt for “custom and automatic installation,” it is always recommended that you go with this option as this would close the other programs that might get installed along with it .So to secure all these issue use the best anti-adware ITL.
Also read How To Remove Browser Hijacker manually
How to remove wp-vcd malware from your wordpress
Wp-Vcd Malware utilizes Pirated Premium WordPress Themes to taint.
New malware is making its essence felt and affecting WordPress that got the pace recently is utilizing nulled (pilfered) premium topics to spread its wings.

Sucuri security scientist Denis Sinegubko says that it has uncovered another type of the well known malware wp-vcd that infuses noxious WordPress administrator clients into responsive or hacked sites.Use Best Free Anti Malware software To protect your system.
According to Sucuri wp-malware preloaded with a pilfered premium form of WordPress topics which offers free download on a few destinations known for giving WordPress center records, for example, functions.php and class.wp.php pilfered subjects, modules, and contents for different CMS stages.
Read How to remove Browser Hijacker from Window 7
Wp-vcd being somewhat unique in the usefulness — sneaks into the framework when it includes a mystery administrator client record to the destinations bolstered, with the username 100010010.
Cybercriminals take help of such camflouged and mystery record to get appended to the contaminated sites so they can exchange the predefined scripted assaults on later dates which can profit them in the more drawn out run.
Wp-vcd used to infuse spam on tainted destinations
Sucuri of Sinegubko saw a restoration of the wp-vcd malware in late November, in this stage, the cybercriminals used wp-vcd as an indirect access records to embed spam connects on defiled destinations.
Read Is browser hijacker a virus?
Wp-vcd produces counterfeit messages which divert the clients to the locales offering the pilfered topics, helping wp-vcd designers spread improve their malware and increment the system of hacked destinations.
Wp-vcd disease is effectively discernable in the contaminated and pilfered subjects. The Sucuri authority feel is it trying to perceive pilfered subjects that are hustled with the wp-vcd malware.
According to his perception, this malware makes a considerable measure of perplexity to the casualty in light of the fact that the records affected have one date, yet two documents have a substitute, or later date, he says. The two same record or archives works on the .php and class.theme-modules.php, these two documents that were contaminated with wp-vcd since mid-July 2017 which was found by an Italian examiner who was chipping away at fathoming this malware.
Sinegubko says, In the event that you survey these tainted documents, you'll presume that functions.php has a similar line of code at the best.
php if (file_exists(dirname(__FILE__) . 'class.theme-modules.php')) include_once(dirname(__FILE__) . 'class.theme-modules.php');

Get Best Antivirus for windows 10 and 7
It is a perception that few WordPress subjects can be expensive for a few clients, site proprietors ought to dependably have at the top of the priority list that in the event that they're not paying for the item and utilizing it for nothing, at that point they may wind up being simply the casualty.
What happens when this malware assault any site
On the off chance that this malware targets and assault any site, the digital programmer gains a mystery another administrator client named 100010010.
Cybercriminals embedded malignant code to change into WordPress center records like .php and class.wp.php and the dubious part is whether you need to erase and evacuate this malware code shape functions.php document, the code again includes in the wake of sparing alter document. You can't completely get rid of the content before expel to the principle WP-VCD document. Some web-assailants infuses pop notice into your site. So to take these fly up promotions utilize the best fly up blocker.
By what method can WP-VCD malware be expelled from my site or subject and modules
- This malware infuses in excellent free subject adaptation, so be watchful before utilizing premium topics free by downloading untrusted sites.
- It is fitting to have a dependable move down, and hostile to infection introduced on the framework, for this reason introduce the best antivirus on 2018 known as ITL which viably filters and erase all the infection assaults.
- The main prudent advance is to expel WP-VCD content from the assaulted site. Our proposal is our free malware evacuation apparatus which will clean your tainted PC and its segments